While researching the weak entropy generated by bx using the Mersenne Twister algorithm, we learned fairly quickly that the generation algorithm is only a minor code change away from re-creating the weak wallets of the Trust Wallet software. Naturally, we spent some time in the last months to see which weak wallets we could summon from the cryptographic realms 🔮🪄.
There is a lot to tell about new discoveries that resulted from this, so we’ll start by presenting some initial statistics and descriptions about the over 2700 weak wallet private keys in these new areas.
Table of Contents
New Research: Trust Wallet-like BIP39 Range
In our original technical writeup, we mentioned the Trust Wallet vulnerability and the surprising similarities between the bx seed-generated weak keys and the Trust Wallet-generated weak keys. There is just one minor algorithmic change in the Pseudo Random Number Generator (PRNG) steps to get weak entropy for one or the other.
So we started crunching away on the numbers to find the weak Trust Wallet accounts.
Here is a basic overview of discovered wallet usage on Bitcoin:
| BIP39 entropy bit length mnemonic length |
128 bit 12 words |
192 bit 18 words |
256 bit 24 words |
|---|---|---|---|
m/44'/0'/0'/0/0 path, compressed pubkey, P2PKH |
215 | 1 | 22 |
m/44'/0'/0'/0/0 path, uncompressed pubkey, P2PKH |
0 | 0 | 0 |
m/49'/0'/0'/0/0 path, P2SH-P2WPKH |
1969 | 0 | 12 |
m/84'/0'/0'/0/0 path, P2WPKH |
412 + 1 | 1 | 2 |
| sum of unique wallet private keys | 2580 | 2 | 36 |
Data details (click to unfold)
- Wallet generation: “Trust Wallet” style MT19937-32 PRNG, PRNG -> BIP39 -> BIP32.
- 15 wallets with 128 bit mnemonics used more than one known derivation path.
- The first deposit into this range happens 2018-04-13.
Overall, we found 2618 wallets in this range so far. As far as we know, the weak PRNG implementation that Trust Wallet temporarily used for new wallets only generates 128 bit (12 word) BIP39 mnemonics, and many of the discovered wallets predate the introduction of the flaw into the Trust Wallet software. Therefore, it seems another wallet generation software uses exactly the same flawed PRNG method!
We expected this, since Ledger Donjon remarked on this as well in their writeup from April 2023:
During our investigations, we also noticed that a few addresses were vulnerable while they had been generated a long time before the Trust Wallet release. That probably means this vulnerability exists in some other wallet implementations which is concerning…
If we look at just the wallets based on 12 word mnemonics between the time of the Trust Wallet vulnerability disclosure and now, the picture is as follows. An (unclear) portion of the “outgoing” funds represents the thefts:
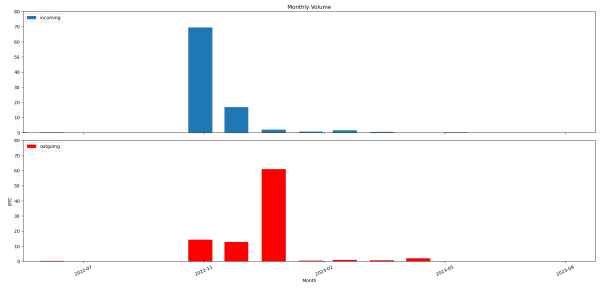
That’s a decent amount of volume overall: somewhere on the order of 90 BTC which plausibly belong to Trust Wallet users were moved in and out of those wallets. The movements correspond to about 2400 individual transactions (not shown).
However, if we zoom out, things get even more interesting:
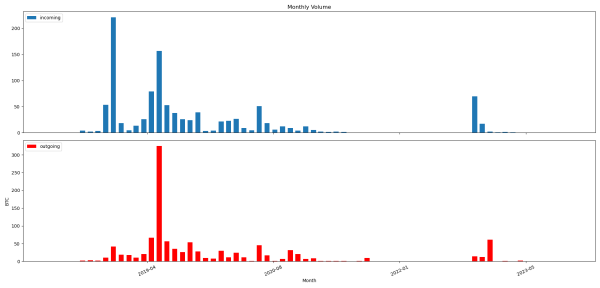
From late 2018 to late 2021, this wallet range was very actively used, with on the order of 975 BTC flowing in and out, distributed over >21300 individual transactions. The Trust Wallet-related funds on the right show the scale of this prior usage, although the Bitcoin price also changed drastically over this whole time period, which affected the amounts as well.
From what we know so far, the most plausible explanation for us is that some other, unknown, wallet software was flawed, and millions of dollars in Bitcoins were stored insecurely. However, no one noticed in time to steal them before they were spent normally 😵💫.
Based on our current data, we suspect the most costly Bitcoin part of the Trust Wallet hack happened on 2023-01-11, when about 200 consecutive transfers moved out about 50 BTC worth within a 30 minute window. Please consider this as an early estimate, especially considering that the corresponding dollar value would be multiple times higher than the approximately $170000 USD figure given by the Trust Wallet team in April 2023 as part of their post-mortem.
List of suspicious withdrawal transactions (click to unfold)
Selection of ten most significant Bitcoin transactions in the suspicious time frame:
| Transaction | Volume | approx. USD @ tx time | Date |
|---|---|---|---|
| a2a028d9..6d469fb4 | -16,060 BTC | -$280.036 | 2023-01-11 20:23:58 |
| 185aa60c..53d3e739 | -8,574 BTC | -$149.502 | 2023-01-11 20:23:58 |
| 23a52b1d..2717279a | -3,439 BTC | -$59.959 | 2023-01-11 20:23:58 |
| f774e14a..f73b6efa | -2,133 BTC | -$37.195 | 2023-01-11 20:23:58 |
| d9781bc9..f6366c41 | -1,579 BTC | -$27.532 | 2023-01-11 20:23:58 |
| caabba1b..2c90d1c8 | -1,346 BTC | -$23.475 | 2023-01-11 20:23:58 |
| 8941e9c3..d6d0b1ce | -1,002 BTC | -$17.473 | 2023-01-11 20:23:58 |
| 104a98c1..31a9f14e | -0,897 BTC | -$15.643 | 2023-01-11 20:05:26 |
| 66cfaa0c..789b99e8 | -0,570 BTC | -$9.947 | 2023-01-11 20:23:58 |
| 464fd34b..b53f3cc3 | -0,524 BTC | -$9.138 | 2023-01-11 20:23:58 |
There’s more to tell here, and we’ll talk more about this range of weak wallets in a future blog post.
New Research: Trust Wallet-like ec-new Range
After finding clear evidence of other wallet software using the same flawed “Trust Wallet”-style of consuming Mersenne Twister MT19937 entropy, we extended our search to the special BIP39-less wallet generation mode that we saw used with bx previously. To describe this range, we’re referring to it as Trust Wallet-like, in terms of Mersenne Twister output usage, and ec-new-like in the basic key generation pattern. However, note that the discovered wallets may not relate to either software, and mostly pre-date Trust Wallet’s temporary use of the weak PRNG mechanism for wallet generation.
Without knowing what other wallet software was involved, this is the next best naming scheme we picked.
Discovered Bitcoin wallets:
| entropy bit length | 128 bit | 192 bit | 256 bit | 2048 bit |
|---|---|---|---|---|
number of walletsm/ path, compressed pubkey, P2PKH |
1 | 84 | 1 | 2 |
number of walletsm/ path, uncompressed pubkey, P2PKH |
0 | 8 | 0 | 0 |
In summary, we found 96 of these wallets so far.
Data details (click to unfold)
- Wallet generation: “Trust Wallet” style MT19937-32 PRNG, PRNG -> BIP32.
- As with the
bxec-newrange, we spotted an unusual outlier that went beyond the normal 256 bit of key size. In theec-newBIP32 usage mode, there is no clear standard on how large or small private keys are allowed to be, but an 2048 bit secp256k1 key is still unusual. If the wallet owners had hoped for some additional security protection, they were clearly disappointed: this wallet is based on the same weak 32 bits of PRNG seeding as the others, unfortunately. - We did not find any wallets in the following bit length range variations: 160 bit, 224 bit, 384 bit, 512 bit, 1024 bit, 4096 bit while searching for compressed public key P2PKH wallets on the base path.
Looking at the on-chain facts for these wallets (discovered so far), we can see that:
- The first deposit into this range happens 2017-04-21.
- The highest overall available aggregated balance was available from mid-2019 to late-2019 with ca. 101.25 BTC.
- Overall, an estimated 110.85 BTC total moved through the weak wallets of this range across their history (this number may miss or double-count some funds).
Movement of funds on discovered Bitcoin wallets:
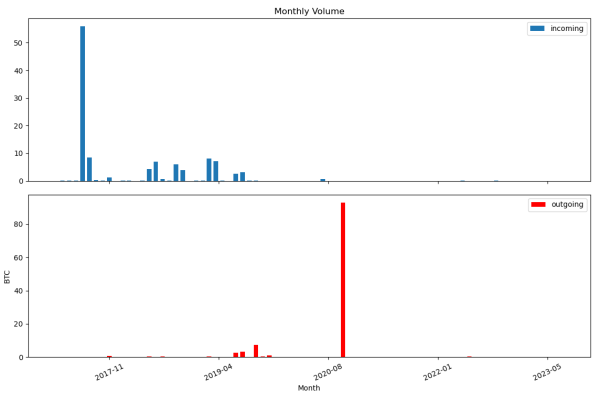
There are a series of 10 transactions around 2020-11-22 which abruptly move out near 93 BTC, close to all of the remaining assets in this range at the time. We’re unclear if this is a legitimate withdrawal or an early theft based on re-calculated weak private keys, but it looks very sudden and comprehensive.
It’s possible that multiple large wallets belonged to the same person and they moved it out during Bitcoin’s price historic price increase that year. A deliberate theft doesn’t really fit the overall time line of the other weak wallet ranges - this is two years “too early” for the known weak wallet thefts, and there is no corresponding large movement of funds on other weak ranges we found during our initial checks. Additionally, patterns in some of the stored amounts (2.75 - 3.0 BTC each) suggest that a significant percentage of them were controlled by a single source.
List of fast withdrawal transactions (click to unfold)
| Transaction | Volume | Date |
|---|---|---|
| 2cca73bc..901033a2 | -6.817 BTC | 2020-11-22 20:04 |
| d834b727..cce083b6 | -64.307 BTC | 2020-11-22 20:04 |
| 8660e093..076bbc4c | -3.5 BTC | 2020-11-22 20:04 |
| c52d0e90..07e1720e | -8.0 BTC | 2020-11-22 20:04 |
| 08ed7b0f..870d9b2f | -6.035 BTC | 2020-11-22 20:04 |
| a9b32f33..06c7bd77 | -0.023 BTC | 2020-11-22 20:07 |
| 4bb53fda..d9c76edd | -0.017 BTC | 2020-11-22 20:07 |
| 6b898c39..219e7a1c | -2.0 BTC | 2020-11-22 20:07 |
| 93f9a63e..d802377c | -0.64 BTC | 2020-11-22 20:07 |
| 1e4065fe..60d460ac | -1.54 BTC | 2020-11-22 20:07 |
Uncompressed Public Keys on P2PKH
During recent work, we noticed that our wallet searches for Pay-To-Public-Key-Hash (P2PKH) addresses had assumed the public key to be in compressed form (33 byte length). This is the modern and common way to generate P2PKH addresses from derived public keys. However, it is not the only way - there is a second canonical form which calculates the hash over the public key in uncompressed form (65 byte length), which results in a different hash and therefore different address.
We’ve done some new searches to cover these variants and found a few previously missed wallets, mostly in ec-new-style ranges. The previous blog post has also been updated with the new data.
For some context on how those could be generated originally, the bx ec-to-public command in the special bx ec-to-public --uncompressed mode could have been involved, at least on the bx ec key range. Other wallet software may have similar legacy address encoding settings.
Summary & Outlook
In this post, we provided some impact details relating to the publicly known Trust Wallet vulnerability, as well as new data on an older, not widely reported or researched wallet software vulnerability in the same BIP39 128 bit range. Similarly, we have shown some statistics and details of wallets in the related ec-new range, which most likely also come from a yet unknown wallet software vulnerability. Finally, we described a less common but relevant Bitcoin Pay-To-Public-Key-Hash address variant that is useful to know for wallet search operations of this type.
We’re working on new topics around the Trust Wallet-related weak wallet ranges. The next blog post will focus more on the development and data source side of our work. Check out our RSS feed if you want to get notified by your favorite reader application.